IT Security Policy Template
Document content
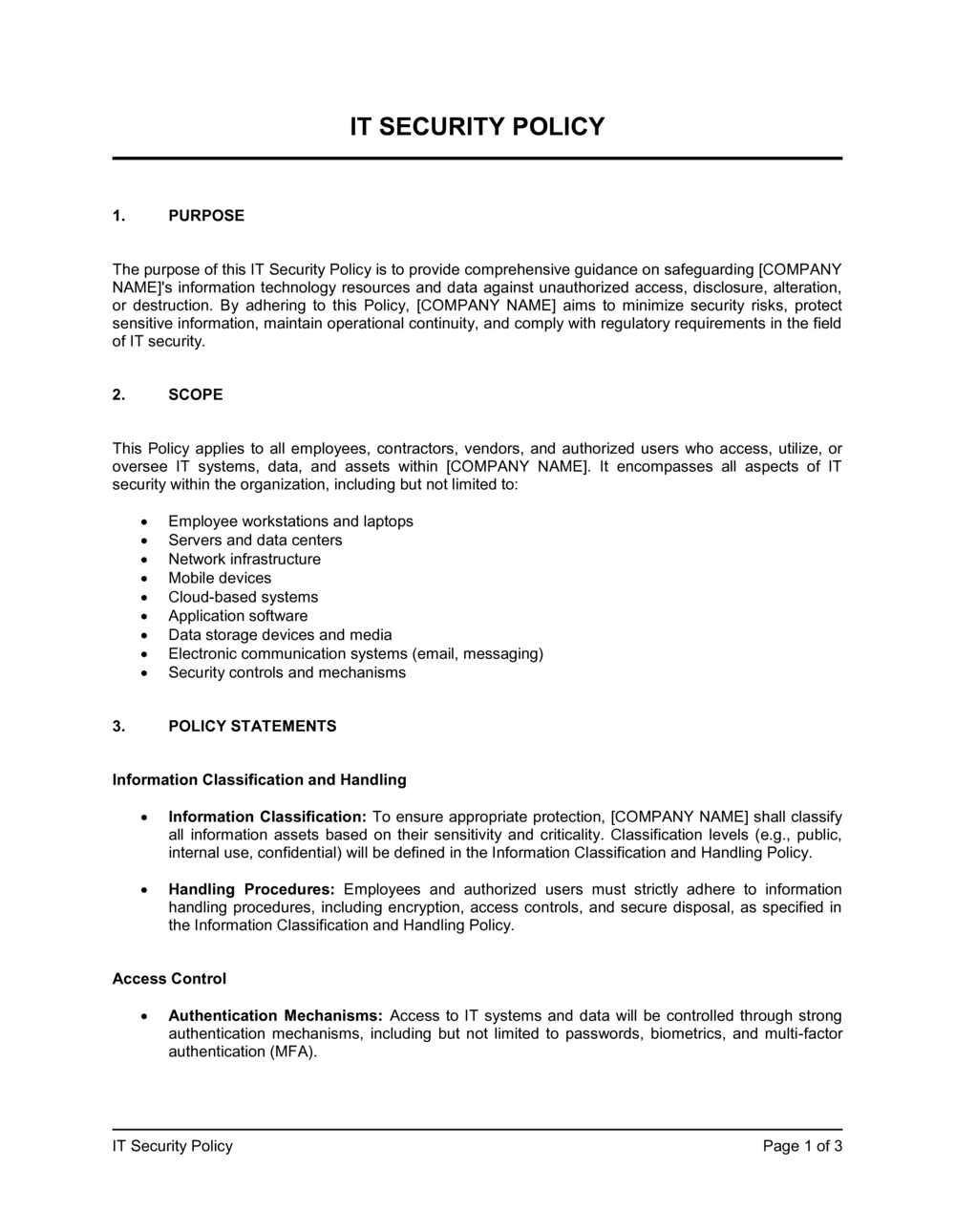
This it security policy template has 3 pages and is a MS Word file type listed under our human resources documents.
Sample of our it security policy template:
IT SECURITY POLICY PURPOSE The purpose of this IT Security Policy is to provide comprehensive guidance on safeguarding [COMPANY NAME]'s information technology resources and data against unauthorized access, disclosure, alteration, or destruction. By adhering to this Policy, [COMPANY NAME] aims to minimize security risks, protect sensitive information, maintain operational continuity, and comply with regulatory requirements in the field of IT security. SCOPE This Policy applies to all employees, contractors, vendors, and authorized users who access, utilize, or oversee IT systems, data, and assets within [COMPANY NAME]. It encompasses all aspects of IT security within the organization, including but not limited to: Employee workstations and laptops Servers and data centers Network infrastructure Mobile devices Cloud-based systems Application software Data storage devices and media Electronic communication systems (email, messaging) Security controls and mechanisms POLICY STATEMENTS Information Classification and Handling Information Classification: To ensure appropriate protection, [COMPANY NAME] shall classify all information assets based on their sensitivity and criticality. Classification levels (e.g., public, internal use, confidential) will be defined in the Information Classification and Handling Policy. Handling Procedures: Employees and authorized users must strictly adhere to information handling procedures, including encryption, access controls, and secure disposal, as specified in the Information Classification and Handling Policy. Access Control Authentication Mechanisms: Access to IT systems and data will be controlled through strong authentication mechanisms, including but not limited to passwords, biometrics, and multi-factor authentication (MFA). Least Privilege: Access privileges will be assigned based on the principle of least privilege (PoLP). Users will only have access to the resources necessary to perform their job responsibilities. Access Reviews: [COMPANY NAME] will conduct regular access reviews and audits to ensure adherence to access control policies and to promptly revoke access for employees and users who no longer require it. Data Protection Data Encryption: Sensitive data, both in transit and at rest, must be protected through encryption. Encryption will be applied during data transmission over networks and when storing data on electronic media. Backup and Recovery: Robust backup and disaster recovery procedures will be established and regularly tested to ensure data availability in case of system failures, data corruption, or data breaches. Malware Protection
3,000+ Templates & Tools to Help You Start, Run & Grow Your Business

Document content
This it security policy template has 3 pages and is a MS Word file type listed under our human resources documents.
Sample of our it security policy template:
IT SECURITY POLICY PURPOSE The purpose of this IT Security Policy is to provide comprehensive guidance on safeguarding [COMPANY NAME]'s information technology resources and data against unauthorized access, disclosure, alteration, or destruction. By adhering to this Policy, [COMPANY NAME] aims to minimize security risks, protect sensitive information, maintain operational continuity, and comply with regulatory requirements in the field of IT security. SCOPE This Policy applies to all employees, contractors, vendors, and authorized users who access, utilize, or oversee IT systems, data, and assets within [COMPANY NAME]. It encompasses all aspects of IT security within the organization, including but not limited to: Employee workstations and laptops Servers and data centers Network infrastructure Mobile devices Cloud-based systems Application software Data storage devices and media Electronic communication systems (email, messaging) Security controls and mechanisms POLICY STATEMENTS Information Classification and Handling Information Classification: To ensure appropriate protection, [COMPANY NAME] shall classify all information assets based on their sensitivity and criticality. Classification levels (e.g., public, internal use, confidential) will be defined in the Information Classification and Handling Policy. Handling Procedures: Employees and authorized users must strictly adhere to information handling procedures, including encryption, access controls, and secure disposal, as specified in the Information Classification and Handling Policy. Access Control Authentication Mechanisms: Access to IT systems and data will be controlled through strong authentication mechanisms, including but not limited to passwords, biometrics, and multi-factor authentication (MFA). Least Privilege: Access privileges will be assigned based on the principle of least privilege (PoLP). Users will only have access to the resources necessary to perform their job responsibilities. Access Reviews: [COMPANY NAME] will conduct regular access reviews and audits to ensure adherence to access control policies and to promptly revoke access for employees and users who no longer require it. Data Protection Data Encryption: Sensitive data, both in transit and at rest, must be protected through encryption. Encryption will be applied during data transmission over networks and when storing data on electronic media. Backup and Recovery: Robust backup and disaster recovery procedures will be established and regularly tested to ensure data availability in case of system failures, data corruption, or data breaches. Malware Protection
Easily Create Any Business Document You Need in Minutes.
Access over 3,000+ business and legal templates for any business task, project or initiative.
Customize your ready-made business document template and save it in the cloud.
Share your files and folders with your team. Create a space of seamless collaboration.
Templates and Tools to Manage Every Aspect of Your Business.
Business in a Box Covers Every Business Department
Includes 16 Types of Business Documents You Need
and Achieve Your Business Goals Faster.
