GDPR Internal Security Policy Template
Document content
This gdpr internal security policy template has 3 pages and is a MS Word file type listed under our human resources documents.
Sample of our gdpr internal security policy template:
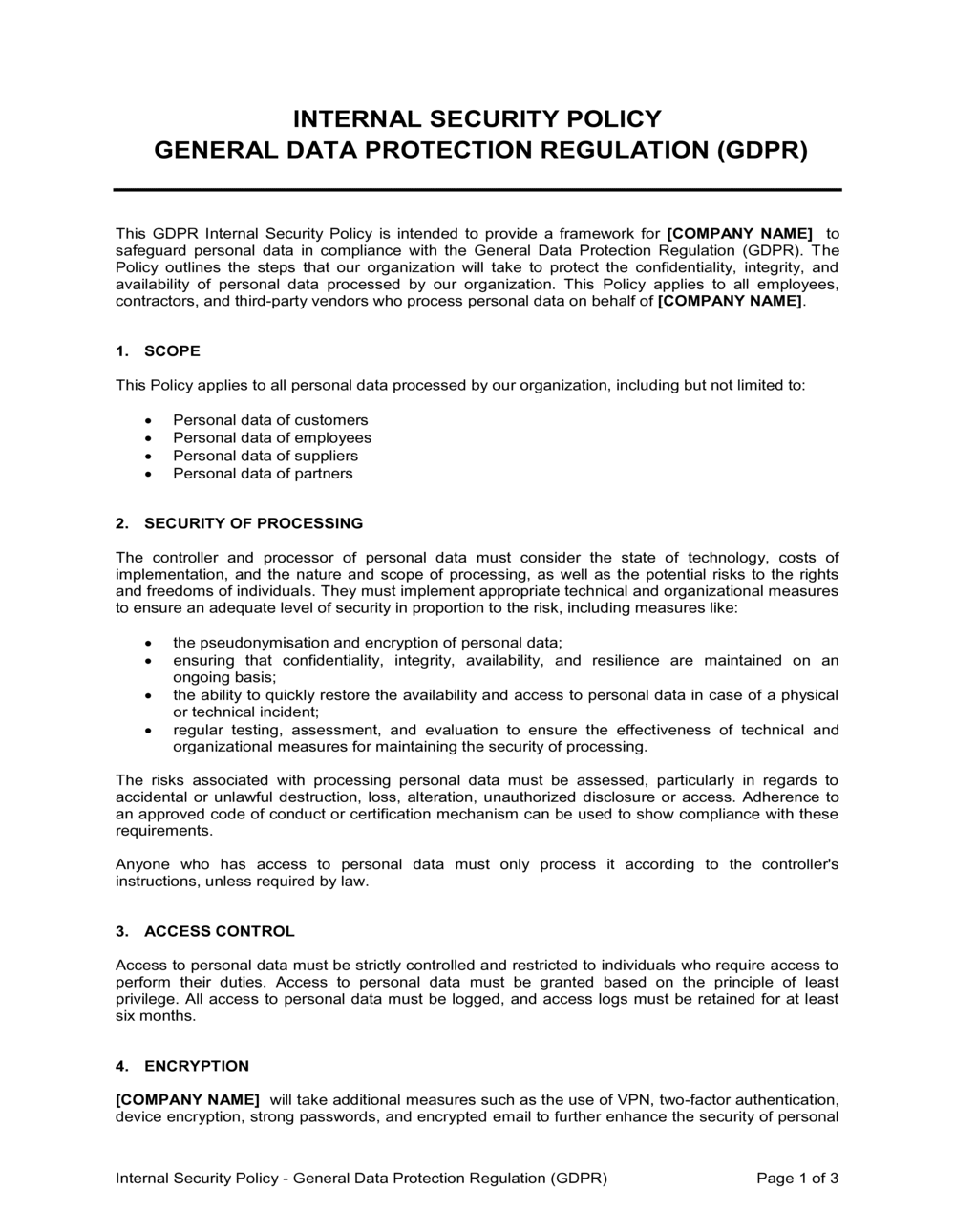
INTERNAL SECURITY POLICY GENERAL DATA PROTECTION REGULATION (GDPR) This GDPR Internal Security Policy is intended to provide a framework for [COMPANY NAME] to safeguard personal data in compliance with the General Data Protection Regulation (GDPR). The Policy outlines the steps that our organization will take to protect the confidentiality, integrity, and availability of personal data processed by our organization. This Policy applies to all employees, contractors, and third-party vendors who process personal data on behalf of [COMPANY NAME]. SCOPE This Policy applies to all personal data processed by our organization, including but not limited to: Personal data of customers Personal data of employees Personal data of suppliers Personal data of partners SECURITY OF PROCESSING The controller and processor of personal data must consider the state of technology, costs of implementation, and the nature and scope of processing, as well as the potential risks to the rights and freedoms of individuals. They must implement appropriate technical and organizational measures to ensure an adequate level of security in proportion to the risk, including measures like: the pseudonymisation and encryption of personal data; ensuring that confidentiality, integrity, availability, and resilience are maintained on an ongoing basis; the ability to quickly restore the availability and access to personal data in case of a physical or technical incident; regular testing, assessment, and evaluation to ensure the effectiveness of technical and organizational measures for maintaining the security of processing. The risks associated with processing personal data must be assessed, particularly in regards to accidental or unlawful destruction, loss, alteration, unauthorized disclosure or access. Adherence to an approved code of conduct or certification mechanism can be used to show compliance with these requirements. Anyone who has access to personal data must only process it according to the controller's instructions, unless required by law. ACCESS CONTROL Access to personal data must be strictly controlled and restricted to individuals who require access to perform their duties. Access to personal data must be granted based on the principle of least privilege. All access to personal data must be logged, and access logs must be retained for at least six months. ENCRYPTION [COMPANY NAME] will take additional measures such as the use of VPN, two-factor authentication, device encryption, strong passwords, and encrypted email to further enhance the security of personal data. The VPN will ensure secure access to the organization's network from remote locations, while two-factor authentication will add an extra layer of security to verify the identity of users. Device encryption will enable the organization to manage and control devices that access personal data
Reviewed on

Document content
This gdpr internal security policy template has 3 pages and is a MS Word file type listed under our human resources documents.
Sample of our gdpr internal security policy template:
INTERNAL SECURITY POLICY GENERAL DATA PROTECTION REGULATION (GDPR) This GDPR Internal Security Policy is intended to provide a framework for [COMPANY NAME] to safeguard personal data in compliance with the General Data Protection Regulation (GDPR). The Policy outlines the steps that our organization will take to protect the confidentiality, integrity, and availability of personal data processed by our organization. This Policy applies to all employees, contractors, and third-party vendors who process personal data on behalf of [COMPANY NAME]. SCOPE This Policy applies to all personal data processed by our organization, including but not limited to: Personal data of customers Personal data of employees Personal data of suppliers Personal data of partners SECURITY OF PROCESSING The controller and processor of personal data must consider the state of technology, costs of implementation, and the nature and scope of processing, as well as the potential risks to the rights and freedoms of individuals. They must implement appropriate technical and organizational measures to ensure an adequate level of security in proportion to the risk, including measures like: the pseudonymisation and encryption of personal data; ensuring that confidentiality, integrity, availability, and resilience are maintained on an ongoing basis; the ability to quickly restore the availability and access to personal data in case of a physical or technical incident; regular testing, assessment, and evaluation to ensure the effectiveness of technical and organizational measures for maintaining the security of processing. The risks associated with processing personal data must be assessed, particularly in regards to accidental or unlawful destruction, loss, alteration, unauthorized disclosure or access. Adherence to an approved code of conduct or certification mechanism can be used to show compliance with these requirements. Anyone who has access to personal data must only process it according to the controller's instructions, unless required by law. ACCESS CONTROL Access to personal data must be strictly controlled and restricted to individuals who require access to perform their duties. Access to personal data must be granted based on the principle of least privilege. All access to personal data must be logged, and access logs must be retained for at least six months. ENCRYPTION [COMPANY NAME] will take additional measures such as the use of VPN, two-factor authentication, device encryption, strong passwords, and encrypted email to further enhance the security of personal data. The VPN will ensure secure access to the organization's network from remote locations, while two-factor authentication will add an extra layer of security to verify the identity of users. Device encryption will enable the organization to manage and control devices that access personal data
Easily Create Any Business Document You Need in Minutes.
Download or open template
Access over 3,000+ business and legal templates for any business task, project or initiative.
Edit and fill in the blanks
Customize your ready-made business document template and save it in the cloud.
Save, Share, Export, or Sign
Share your files and folders with your team. Create a space of seamless collaboration.



